Hackers are getting sophisticated when it comes to phishing scams. Recently, Google Gmail and Microsoft Office users were targets of a phishing attack that included graphics and a login page that were nearly identical to the mentioned providers. These improved tactics increase the likelihood of recipients falling victim to the scam. Here is what to look for:
Google Gmail Scam
This scam targets Gmail users who access their email accounts in a web browser. A graphic is displayed that looks identical to the graphic Google uses to indicate a PDF or Word document attachment, but it embeds the image in the email body itself. When the user clicks on it, he or she is redirected to a page that looks just like the normal Google login screen.
Once the victim enter their username/password, those credentials are then used to gain access to the victim’s Gmail account and further spread the scam.

Microsoft Office 365 Scam
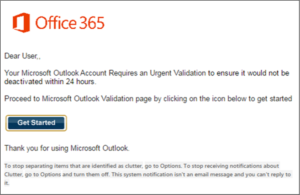
The below email is sent to Microsoft Office 365 account users. Once a victim clicks on the link to “Get Started”, they are presented with a fake Office 365 login screen and directed to enter their Office 365 credentials. If entered, hackers are free to roam the system, installing malware, accessing proprietary business information, and stealing personal and financial customer information.
How Can You Prevent Falling Victim?
- Think before you click. If you get an email that appears to be from legitimate site with a request that you click on a link to visit the site for any reason, including updating your security information, review the request cautiously.
- Check the sender’s email address. The first phishing giveaway is often the sender’s email address. Even if the email itself looks legitimate, that address often stands out as being questionable.
- Typos are a red flag. Cyber-criminals are not vested in copy editing. One of the easiest ways to spot an email sent as part of a phishing attack is typos.
- Contact the Supposed Sender. When in doubt, pick up the phone and call the originating company’s customer service, or send an email directly to their customer service to verify they sent it.
- Invest in Cybersecurity Awareness Training. A good training program includes company simulated phishing attacks that keeps employees aware of new tactics and identifies weak links. The BMT team provides comprehensive training as a service offering, contact us for more information.