European Union military personnel and political leaders working on gender equality initiatives have emerged as the target of a new campaign that delivers an updated version of RomCom RAT called PEAPOD.
Cybersecurity firm Trend Micro attributed the attacks to a threat actor it tracks under the name Void Rabisu, which is also known as Storm-0978, Tropical Scorpius, and UNC2596, and is also believed to be associated with Cuba ransomware.
The adversarial collective is something of an unusual group in that it conducts both financial motivated and espionage attacks, blurring the line between their modes of operation. It’s also exclusively linked to the use of RomCom RAT.
Attacks involving the use of the backdoor have singled out Ukraine and countries that support Ukraine in its war against Russia over the past year.
Earlier this July, Microsoft implicated Void Rabisu to the exploitation of CVE-2023-36884, a remote code execution flaw in Office and Windows HTML, by using specially-crafted Microsoft Office document lures related to the Ukrainian World Congress.
RomCom RAT is capable of interacting with a command-and-control (C&C) server to receive commands and execute them on the victim’s machine, while also packing in defense evasion techniques, marking a steady evolution in its sophistication.
The malware is typically distributed via highly targeted spear-phishing emails and bogus ads on search engines like Google and Bing to trick users into visiting lure sites hosting trojanized versions of legitimate applications.
“Void Rabisu is one of the clearest examples where we see a mix of the typical tactics, techniques, and procedures (TTPs) used by cybercriminal threat actors and TTPs used by nation-state-sponsored threat actors motivated primarily by espionage goals,” Trend Micro said.
The latest set of attacks detected by the company in August 2023 also deliver RomCom RAT, only it’s an updated and slimmed-down iteration of the malware that’s distributed via a website called wplsummit[.]com, which is a replica of the legitimate wplsummit[.]org domain.
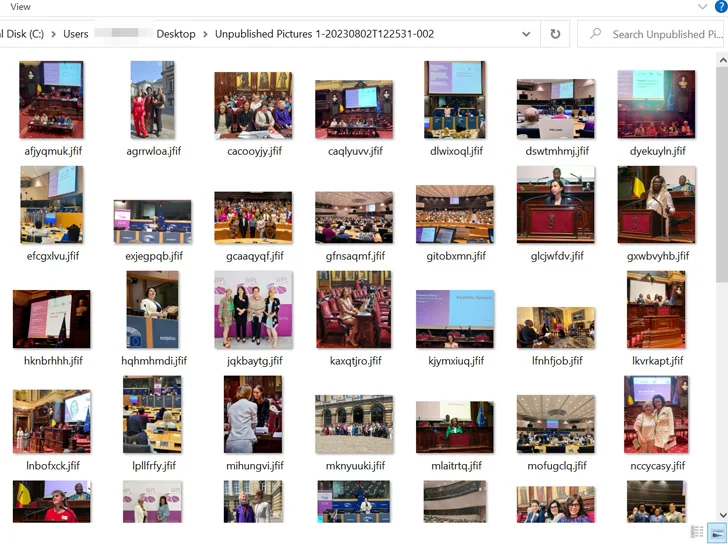
Present on the website is a link to a Microsoft OneDrive folder that hosts an executable named “Unpublished Pictures 1-20230802T122531-002-sfx.exe,” a 21.6 MB file that aims to mimic a folder containing photos from the Women Political Leaders (WPL) Summit that took place in June 2023.
The binary is a downloader that drops 56 pictures onto the target system as a decoy, while retrieving a DLL file from a remote server. These photos are said to have been sourced by the malicious actor from individual posts on various social media platforms such as LinkedIn, X (formerly known as Twitter), and Instagram.
The DLL file, for its part, establishes contact with another domain to fetch the third-stage PEAPOD artifact, which supports 10 commands in total, down from 42 commands supported by its predecessor.
The revised version is equipped to execute arbitrary commands, download and upload files, get system information, and even uninstall itself from the compromised host. By stripping down the malware to the most essential features, the idea is to limit its digital footprint and complicate detection efforts.
“While we have no evidence that Void Rabisu is nation-state-sponsored, it’s possible that it is one of the financially motivated threat actors from the criminal underground that got pulled into cyberespionage activities due to the extraordinary geopolitical circumstances caused by the war in Ukraine,” Trend Micro said.