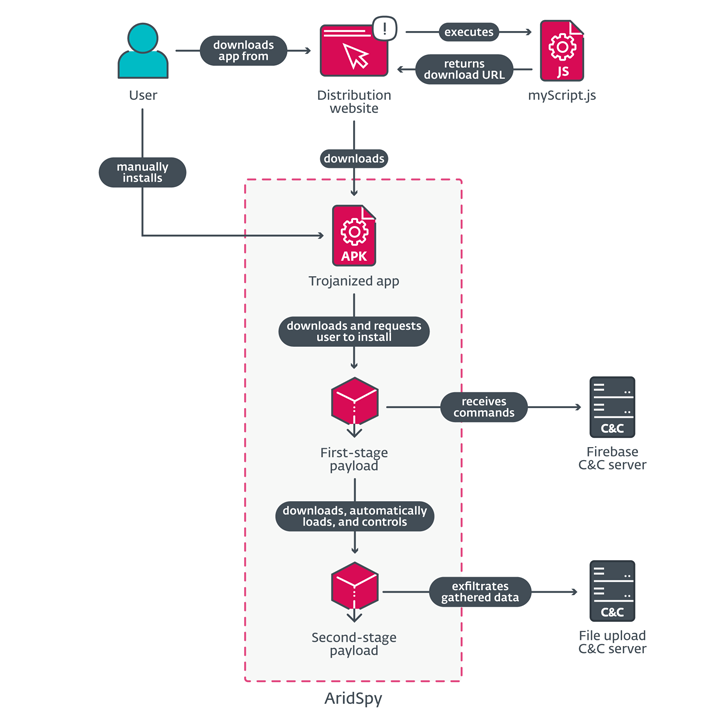
The threat actor known as Arid Viper has been attributed to a mobile espionage campaign that leverages trojanized Android apps to deliver a spyware strain dubbed AridSpy.
“The malware is distributed through dedicated websites impersonating various messaging apps, a job opportunity app, and a Palestinian Civil Registry app,” ESET researcher Lukáš Štefanko said in a report published today. “Often these are existing applications that had been trojanized by the addition of AridSpy’s malicious code.”
The activity is said to have spanned as many as five campaigns since 2022, with prior variants of AridSpy documented by Zimperium and 360 Beacon Labs. Three out of the five campaigns are still active.
Arid Viper, a suspected Hamas-affiliated actor who is also called APT-C-23, Desert Falcon, Grey Karkadann, Mantis, and Two-tailed Scorpion, has a long track record of using mobile malware since its emergence in 2017.
“Arid Viper has historically targeted military personnel in the Middle East, as well as journalists and dissidents,” SentinelOne noted late last year, adding the group “continues to thrive in the mobile malware space.”
ESET’s analysis of the latest version of AridSpy shows that it has been transformed into a multi-stage trojan that can download additional payloads from a command-and-control (C2) server by the initial, trojanized app.
The attack chains mainly involve targeting users in Palestine and Egypt via bogus sites that function as distribution points for the booby-trapped apps.
Some of the fake-but-functional apps claim to be secure messaging services such as LapizaChat, NortirChat, and ReblyChat, each of which is based on legitimate apps like StealthChat, Session, and Voxer Walkie Talkie Messenger, while another app purports to be from the Palestinian Civil Registry.
The website for the Palestinian Civil Registry (“palcivilreg[.]com”), which was registered on May 30, 2023, has been also found to be advertised via a dedicated Facebook page that has 179 followers. The app propagated via the website is inspired by an app of the same name that’s available on the Google Play Store.
“The malicious app available on palcivilreg[.]com is not a trojanized version of the app on Google Play; however, it uses that app’s legitimate server to retrieve information,” Štefanko said. “This means that Arid Viper was inspired by that app’s functionality but created its own client layer that communicates with the legitimate server.”
ESET said it further discovered AridSpy being disseminated under the guise of a job opportunity app from a website (“almoshell[.]website”) registered in August 2023. A notable aspect of the app is that it’s not based on any legitimate app.
Upon installation, the malicious app checks for the presence of security software against a hard-coded list, and proceeds further to download a first-stage payload only if none of them are installed on the device. The payload impersonates an update of Google Play Services.
“This payload works separately, without the necessity of having the trojanized app installed on the same device,” Štefanko explained. “This means that if the victim uninstalls the initial trojanized app, for example LapizaChat, AridSpy will not be in any way affected.”
The main responsibility of the first-stage is to download the next-stage component, which harbors the malicious functionality and makes use of a Firebase domain for C2 purposes.
The malware supports a wide range of commands to harvest data from the devices and can even deactivate itself or perform exfiltration when on a mobile data plan. Data exfiltration is initiated either by means of a command or when a specifically defined event is triggered.
“If the victim locks or unlocks the phone, AridSpy will take a picture using the front camera and send it to the exfiltration C&C server,” Štefanko said. “Pictures are taken only if it is more than 40 minutes since the last picture was taken and the battery level is above 15%.”