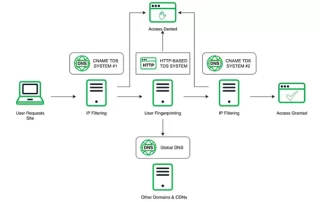
Phish-Friendly Domain Registry “.top” Put on Notice
The Chinese company in charge of handing out domain names ending in “.top” has been given until mid-August 2024 to show that it has put in place systems for managing phishing reports and suspending abusive domains, or else forfeit its license to sell domains. The warning comes amid the release [...]