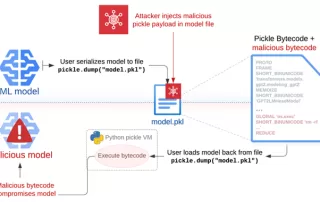
Cybercriminals Exploit Free Software Lures to Deploy Hijack Loader and Vidar Stealer
Threat actors are luring unsuspecting users with free or pirated versions of commercial software to deliver a malware loader called Hijack Loader, which then deploys an information stealer known as Vidar Stealer. "Adversaries had managed to trick users into downloading password-protected archive files containing trojanized copies of a Cisco [...]