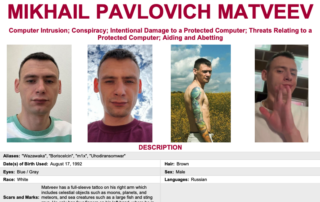
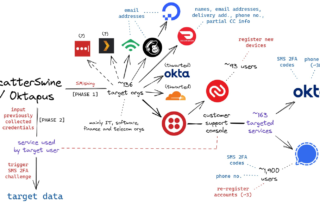
Safety Tips for Online Holiday Shoppers!
Tis the Season for Holiday Scammers! 3 Useful Tips When Shopping Online Holiday shopping is in full swing! We wanted to let you know about a few online shopping trends we've noticed and give some tips about how to stay safe online while buying gifts for everyone on your list! [...]