Cybersecurity experts have shed light on a new cybercrime group known as ShadowSyndicate (formerly Infra Storm) that may have leveraged as many as seven different ransomware families over the past year.
“ShadowSyndicate is a threat actor that works with various ransomware groups and affiliates of ransomware programs,” Group-IB and Bridewell said in a new joint report.
The actor, active since July 16, 2022, has linked to ransomware activity related to Quantum, Nokoyawa, BlackCat, Royal, Cl0p, Cactus, and Play strains, while also deploying off-the-shelf post-exploitation tools like Cobalt Strike and Sliver as well as loaders such as IcedID and Matanbuchus.
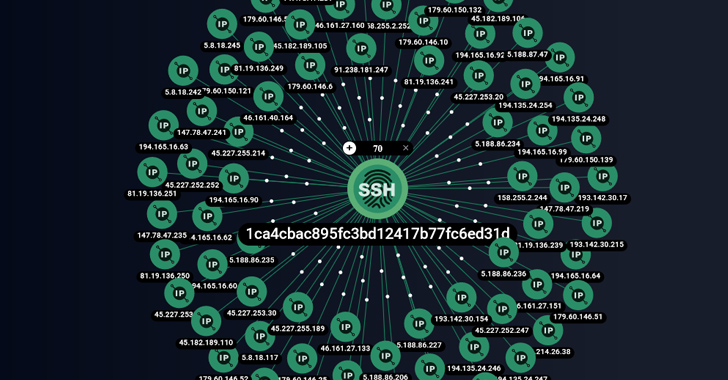
The findings are based on a distinct SSH fingerprint (1ca4cbac895fc3bd12417b77fc6ed31d) discovered on 85 servers, 52 of which have been used as command-and-control (C2) for Cobalt Strike. Among those servers are eight different Cobalt Strike license keys (or watermarks).
A majority of the servers (23) are located in Panama, followed by Cyprus (11), Russia (9), Seychelles (8), Costa Rica (7), Czechia (7), Belize (6), Bulgaria (3), Honduras (3), and the Netherlands (3).
Group-IB said it also found additional infrastructure overlaps that connect ShadowSyndicate to TrickBot, Ryuk/Conti, FIN7, and TrueBot malware operations.
“Out of the 149 IP addresses that we linked to Cl0p ransomware affiliates, we have seen, since August 2022, 12 IP addresses from 4 different clusters changed ownership to ShadowSyndicate, which suggests that there is some potential sharing of infrastructure between these groups,” the companies said.
The disclosure comes as the German law enforcement authorities announced a second targeted strike against actors associated with the DoppelPaymer ransomware group, some of whom were targeted earlier this March, executing search warrants against two suspects in Germany and Ukraine.
The individuals, a 44-year-old Ukrainian and a 45-year-old German national, are alleged to have held key responsibilities within the network and received illicit proceeds from the ransomware attacks. Their names were not disclosed.
The development also follows a joint advisory issued by the U.S. Federal Bureau of Investigation (FBI) and the Cybersecurity and Infrastructure Security Agency (CISA) about a double extortion actor called Snatch (formerly Team Truniger) that has targeted a wide range of critical infrastructure sectors since mid-2021.
“Snatch threat actors employ several different methods to gain access to and maintain persistence on a victim’s network,” the agencies said, calling out their consistent evolution of tactics and the ability of the malware to evade detection by rebooting Windows systems into Safe Mode.
“Snatch affiliates primarily rely on exploiting weaknesses in Remote Desktop Protocol (RDP) for brute-forcing and gaining administrator credentials to victims’ networks. In some instances, Snatch affiliates have sought out compromised credentials from criminal forums/marketplaces.”
The U.S. Department of Homeland Security (DHS), in its latest Homeland Threat Assessment report, noted that ransomware groups are continuously developing new methods to improve their ability to financially extort victims, making 2023 the second most profitable year after 2021.
“These groups have increased their use of multilevel extortion, in which they encrypt and exfiltrate their targets’ data and typically threaten to publicly release stolen data, use DDoS attacks, or harass the victim’s customers to coerce the victim to pay,” the DHS report said.
Akira is a case in point. The ransomware has expanded its reach since emerging as a Windows-based threat in March 2023 to include Linux servers and VMWare ESXi virtual machines, underscoring its ability to quickly adapt to trends. As of mid-September, the group has successfully hit 110 victims in the U.S. and the U.K.
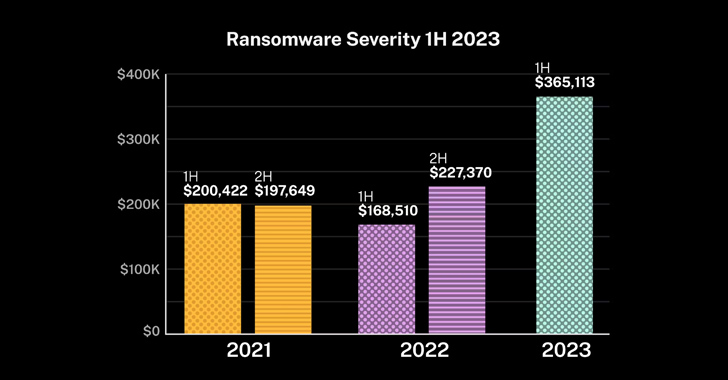
The resurgence of ransomware attacks has also been accompanied by a spike in cyber insurance claims, with overall claims frequency increasing 12% in the first half of the year in the U.S. and victims reporting an average loss amount of more than $365,000, a 61% jump from the second half of 2022.
“Businesses with more than $100 million in revenue saw the largest increase in frequency, and while other revenue bands were more stable, they also faced surges in claims,” cyber insurance firm Coalition said.
The constant flux in the threat landscape is best exemplified by BlackCat, Cl0p, and LockBit, which have remained some of the most prolific and evolutionary ransomware families in recent months, primarily targeting small and large enterprises spanning banking, retail, and transportation sectors. The number of active RaaS and RaaS-related groups has grown in 2023 by 11.3%, rising from 39 to 45.
A report from eSentire last week detailed two LockBit attacks in which the e-crime group was observed leveraging the victim companies’ internet-exposed remote monitoring and management (RMM) tools (or their own) to spread the ransomware across the IT environment or push it to their downstream customers.
The reliance on such living-off-the-land (LotL) techniques is an attempt to avoid detection and confuse attribution efforts by blending malicious and legitimate use of IT management tools, the Canadian company said.
In another instance of a BlackCat attack highlighted by Sophos this month, the attackers were seen encrypting Microsoft Azure Storage accounts after gaining access to an unnamed customer’s Azure portal.
“During the intrusion, the threat actors were observed leveraging various RMM tools (AnyDesk, Splashtop, and Atera), and using Chrome to access the target’s installed LastPass vault via the browser extension, where they obtained the OTP for accessing the target’s Sophos Central account, which is used by customers to manage their Sophos products,” the company said.
“The adversary then modified security policies and disabled Tamper Protection within Central before encrypting the customer’s systems and remote Azure Storage accounts via ransomware executable with the extension .zk09cvt.”