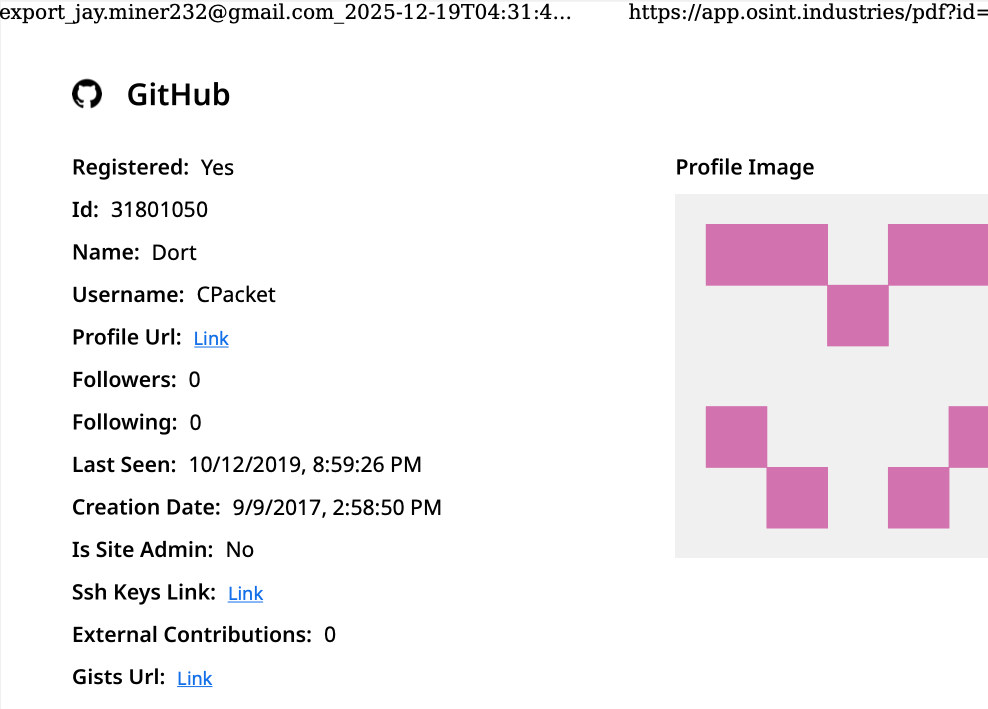
Cybersecurity researchers have discovered a new Apple macOS backdoor called SpectralBlur that overlaps with a known malware family that has been attributed to North Korean threat actors.
“SpectralBlur is a moderately capable backdoor that can upload/download files, run a shell, update its configuration, delete files, hibernate, or sleep, based on commands issued from the [command-and-control] server,” security researcher Greg Lesnewich said.
The malware shares similarities with KANDYKORN (aka SockRacket), an advanced implant that functions as a remote access trojan capable of taking control of a compromised host.
It’s worth noting that the KANDYKORN activity also intersects with another campaign orchestrated by the Lazarus sub-group known as BlueNoroff (aka TA444) which culminates in the deployment of a backdoor referred to as RustBucket and a late-stage payload dubbed ObjCShellz.
In recent months, the threat actor has been observed combining disparate pieces of these two infection chains, leveraging RustBucket droppers to deliver KANDYKORN.
The latest findings are another sign that North Korean threat actors are increasingly setting their sights on macOS to infiltrate high-value targets, particularly those within the cryptocurrency and the blockchain industries.
“TA444 keeps running fast and furious with these new macOS malware families,” Lesnewich said.
Security researcher Patrick Wardle, who shared additional insights into the inner workings of SpectralBlur, said the Mach-O binary was uploaded to the VirusTotal malware scanning service in August 2023 from Colombia.
The functional similarities between KANDYKORN and SpectralBlur have raised the possibility that they may have been built by different developers keeping the same requirements in mind.
What makes the malware stand out are its attempts to hinder analysis and evade detection while using grantpt to set up a pseudo-terminal and execute shell commands received from the C2 server.
The disclosure comes as a total of 21 new malware families designed to target macOS systems, including ransomware, information stealers, remote access trojans, and nation-state-backed malware, were discovered in 2023, up from 13 identified in 2022.
“With the continued growth and popularity of macOS (especially in the enterprise!), 2024 will surely bring a bevy of new macOS malware,” Wardle noted.